
Methics has delivered its high value solutions across EMEA and APAC regions to MNOs, Governments, Application/Service providers, Certificate Authorities and PKI implementors. We offer solutions for Mobile Identity, Mobile Signature Services, PKI services, Document Signing and KYC. Our solutions are comprised of Kiuru Mobile Signature Service Provider (MSSP) Platform, is a complete platform for providing a cost-efficient, managed digital identification and signature service for customers. The solution supports an ecosystem of mobile identities that enables and supports Qualified Electronic Signatures, Advanced Electronic Signatures (AdES) and many other signature formats. It also offers a standard interface to connect applications and online portals of all kinds to the Mobile ID service.
Working Principle
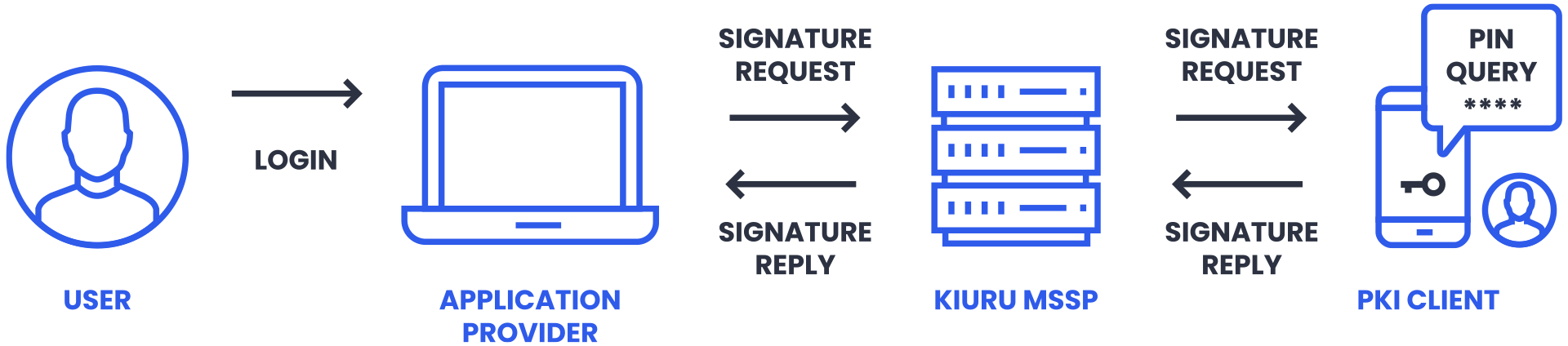
The Mobile User accesses a service which requires strong authentication or digital signatures. To get the user’s digital signature, the Application Provider sends a signature request to an MSSP. The MSSP delivers the request to the Mobile User’s phone, and the User authenticates or signs with their Mobile ID using a PKI Client. The signed request is sent back to the Application Provider through the same channels.
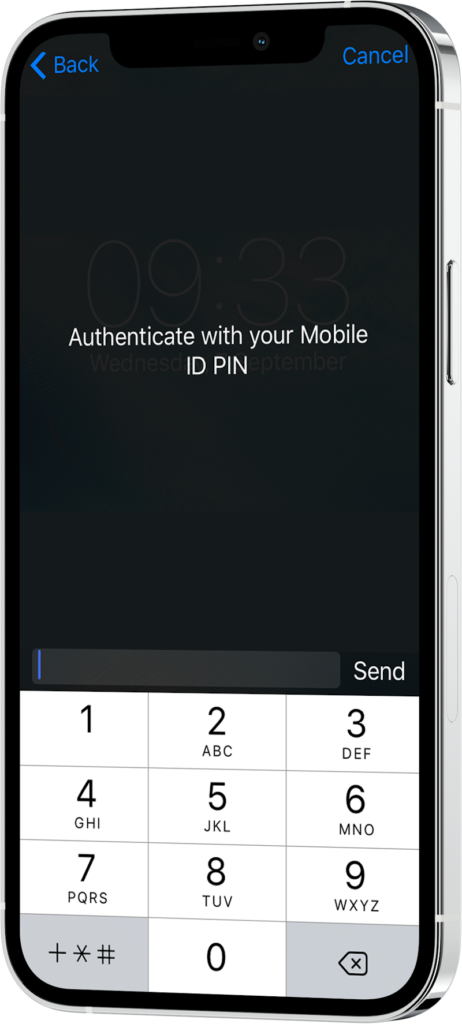
Local Signature (SIM card) Solution
Local Signature is the core functionality such that end user brings and uses their own secure signature-creation device like SIM card or eSIM to create electronic signatures securely. Methics Local Signing Solution helps implement Local Signatures, which can implement a universal strong authentication service.
Methics Local Signing Solution deployments has been been certified in accordance with ETSI TS 102 204 from a leading auditing company, and also have certifications from institutes like KPMG and NIXT.
Alauda P38 PKI Applet
WPKI Client is installed on the SIM card and it provides the interface required for communication with the mobile user and the cryptographic functionalities required for performing the signing of the DTBS, for an MSS transaction.
Kiuru MSSP
The MSSP platform binds together the PKI infrastructure including identity registration and verification, certificate management, cryptography operations, wireless communication, monitoring and event recording. The platform contains a HomeMSSP with built-in OTA to deliver messages to Mobile User.
Remote Signature (Smartphone App) Solution
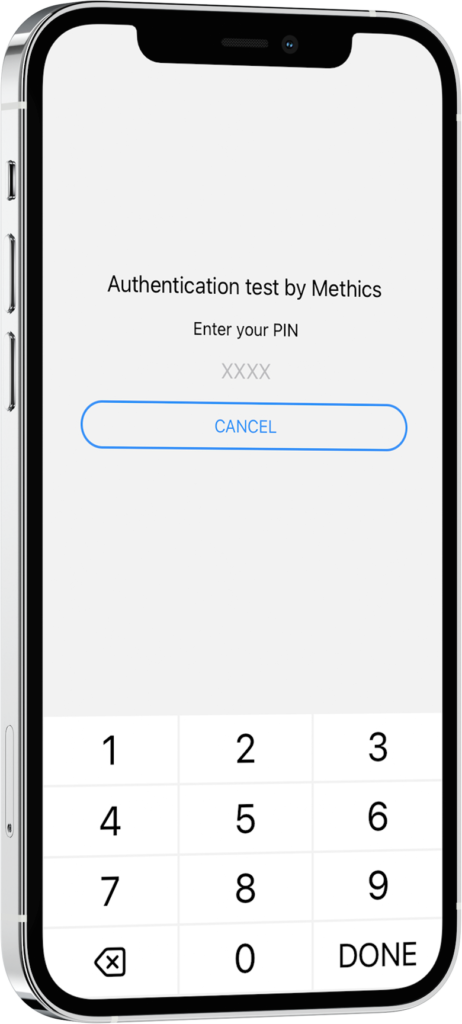
Remote Signing solution provides technology which can implement a universal strong authentication service similar to Local Signing without PKI Sim card. Remote Signature is the core functionality such that end user uses a secure signature creation device remotely to create electronic signatures securely.
Alauda PBY is currently the only PKI Client App on the market whose source code is available for licensing. This enables completely adaptable integration and auditing.
Alauda PBY Smartphone App
Alauda PBY app is a secure signature creation application for smartphones. App uses a server-side Hardware Security Module (HSM) to manage the signing keys. The signing keys are generated by the HSM and split between the HSM and the app. The app supports using signer defined PIN or biometrics to ensure sole control of the signing keys and to create digital signatures.
Kiuru MSSP with Kiuru Signature Activation Module (SAM)
The Kiuru SAM product is a Signature Activation Module (SAM) that offers remote digital signature services. It ensures that the Signer’s signing keys are only used under the sole control of the Signer and only used for the intended purpose.
Unified Signing Solution (Local & Remote Signature)
Unified Signature is a seamlessly joint functionality that Remote Signature and Local Signature can offer together. It provides combination of all best parts of these core functionalities in form of Unified Signing Solution.

Built on Standards
Methics offers solutions for Mobile Identity, Mobile Signature Services, PKI services and Document Signing. Our solution comprises of Kiuru Mobile Signature Service Provider (MSSP) Platform including Remote and Local Signature creation devices. Kiuru MSSP is a complete platform for providing a cost-efficient, managed digital identification and signature service for customers. Methics Unified Signature Solution utilizes Kiuru MSSP v 6.0, Alauda PBY 2.0 and Alauda P38 2.0, eIDAS compliant Kiuru SAM to deliver a standard interface to connect applications and online portals of all kinds to the Mobile ID service.
Multiple WPKI Clients
Unified Signature solution provides wPKI clients like smartphone App, mobile SIM card, eSIM, and CSC connecting API for desktop clients. Solution uses Kiuru Mobile Signature Service Provider (MSSP) platform to establish an open, standard based and secure channel between Alauda Wireless PKI Clients. The tamper-resistant SIM card or eSIM in the phone to deliver strong electronic identities to end users. For smartphones Alauda PBY app acts as a Qualified Signature Creation Device (QSCD).
