Local Signature is the core functionality such that end user brings and uses their own secure signature-creation device like SIM card or eSIM to create electronic signatures securely. It ensures end user’s signing keys (private key) remain in their control.
Mobile Signature Service commonly known as Local Signing or mobile PKI based (SIM card) solution is the only technology which can implement a universal strong authentication service. Solution takes advantage of the most pervasive electronic device (the mobile phone) and the tamper-resistant SIM card in the phone to deliver strong electronic identities to end users. Kiuru Mobile Signature Service Provider (MSSP) platform is used to establish an open, standard based and secure channel between Alauda Wireless PKI Client present inside sim cards. It is an enabling service which provides critical infrastructure for user authentication conforming to the highest available levels of assurances (LoA) for Mobile Network Operators (MNOs), trusted Application/Service providers (AP/SP), Governments and Certificate Authorities.
The secure element contains a wireless PKI Client (e.g Alauda P38) on the SIM card. Methics has a long experience of working with leading SIM card manufactures of the world (such as Gemalto/Thales, Giesecke and Devrient, IDEMIA, XH Smart Tech, Eastcompeace, Workz) to have a standard-based applet Alauda P38 (Alauda B17) work with their cards to perform PKI operations and Local Signing (Remote Signing).
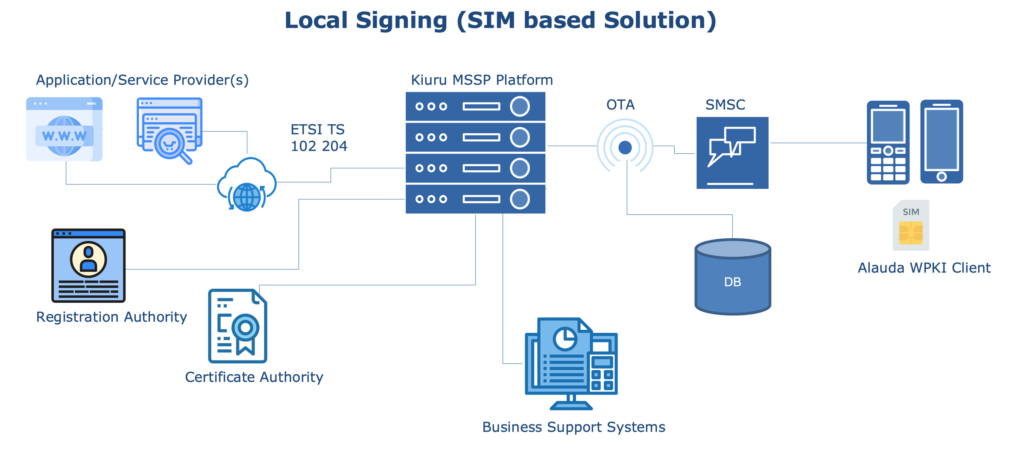
AP/SP are integrated with Kiuru MSSP Platform through ETSI TS 102 204 protocol (SOAP or RESTful). In order to provide secure services to the end user (Mobile Users), they are required by AP/SP to prove their identity. To get the user’s identity/digital signature, the Application Provider sends a signature request to an MSSP. The MSSP delivers the request to the Mobile User’s phone using the WPKI protocol. The User authenticates or signs with their Mobile ID using their WPKI client present in their phones. The signed request is sent back to the Application Provider through the same channels.
The communication from the MSSP to the Alauda Applet and back uses Alauda Encryption. Alauda Encryption uses a dedicated 3DES (or AES) symmetric key pair for message encryption. These keys are similar to OTA keys, and they are installed at the Sim factory during the card personalization phase.
Following best practices, Methics delivers the authentication/signature request to user by following standards such as WYSIWYS. Data To Be Signed (DTBS) is always explicit UTF-8 text, an MSSP may provide additional signed attribute parameters as CMS formatted attributes, like CAdES data element digest of the user certificate. The Alauda Applet can produce various kinds of PKCS#1/ PKCS#7/ PKCS#10 signatures and CMS signature/ countersignature as per [CEN1] [CEN2]. The Alauda Applet uses the standard PKCS#1v1.5 signature primitive and envelope in digital signature production.
Methics Local Signature deployments has been been certified in accordance with ETSI TS 102 204 from a leading auditing company, and also have certifications from institutes like KPMG and NIXT.
If you feel you need some more information to decide which Mobile ID wireless PKI client is good for your service, you can read our article post in detail about PKI security on SIM Applet (Local Signing Solution) and Smartphone App (Remote Signing Solution).
Feel free to get in touch with us if you want a user-friendly software for your TSP, implement authentication/sign in service, document signing solution, or want to increase your user adoption of PKI services.
References:
- OASIS: OASIS paper for DSS Extension for Local Signature Computation Version 1.0
- ETSI TS 102 204
- EN 419 241-1: Trustworthy Systems Supporting Server Signing – Part 1: General System Security Requirements
