Introduction
A Digital Identity is the electronic representation of an individual, organization, or device in the digital world. It is a collection of electronically stored identity attributes and data used to uniquely identify and authenticate entities during or after online transactions. Unique Identification of electronically stored identity attributes is called Electronic Identification (eID).
Electronic Identification (eID) of individuals or legal entities is essential for a secure, convenient, and efficient digital environment to prosper. Digital Identities and eID enables secure access to various services and resources, ensuring trust, security, and privacy in the digital environment.
The electronic identification have been tackled over the years in different pan-European Identity projects. In 2023, with lessons from from eIDAS (electronic IDentification, Authentication and Trust Services), a EU regulation that establishes a legal framework for electronic identification and trust services across EU. Now eIDAS2 is under finalization stages before becoming the law.
While eIDAS does not explicitly define “Digital Identity,” it provides guidelines for electronic identification (eID) schemes and the levels of assurance (LoA) for these schemes. Referring to the set of attributes, credentials, and other data associated which can be used to uniquely identify and authenticate them in electronic transactions.
Digital Identity Lifecycle
Digital Identity lifecycle refers to the process of creating, managing and maintaining the identity over its lifetime. This lifecycle as a continuous process that begins with the creation of a person’s identity when they first register. This electronic identity is then authenticated and their attributes and credentials are updated over time. The life cycle of using an electronic identity ends when the identity record is deactivated or invalidated, for example due to death, a person’s deletion request or other reasons. However, the person’s electronic signature must be able to be verified even after death, because, for example, the person’s will must be able to be verified even after death. In addition, these life cycles are different for both national identity solutions and corporate identity solutions.
Digital Identity of a citizen (user) are issued by the state’s national identity solutions as the citizen’s root identity. National Identity solutions is very country-specific and depends on the country’s historical development, the trustworthiness of existing data registers and other authoritative sources of identity information. Though it can be said with utmost confidence any national Digital Identity system can be divided into four stages to describe it’s lifecycle.
- Registration
- Identity proofing (Presenting a person identity claim and validation of correctness)
- Verification (verification of the identity attributes)
- Identity/Credentials Issuance
- Identity Use
- Verification
- Authentication and
- Authorization
- Identity Management
- Maintenance
- Revocation or Suspension
Image below summarizes the life cycle phases considered for the creation of the digital identity described above. This image is an extract from WorldBank. 1
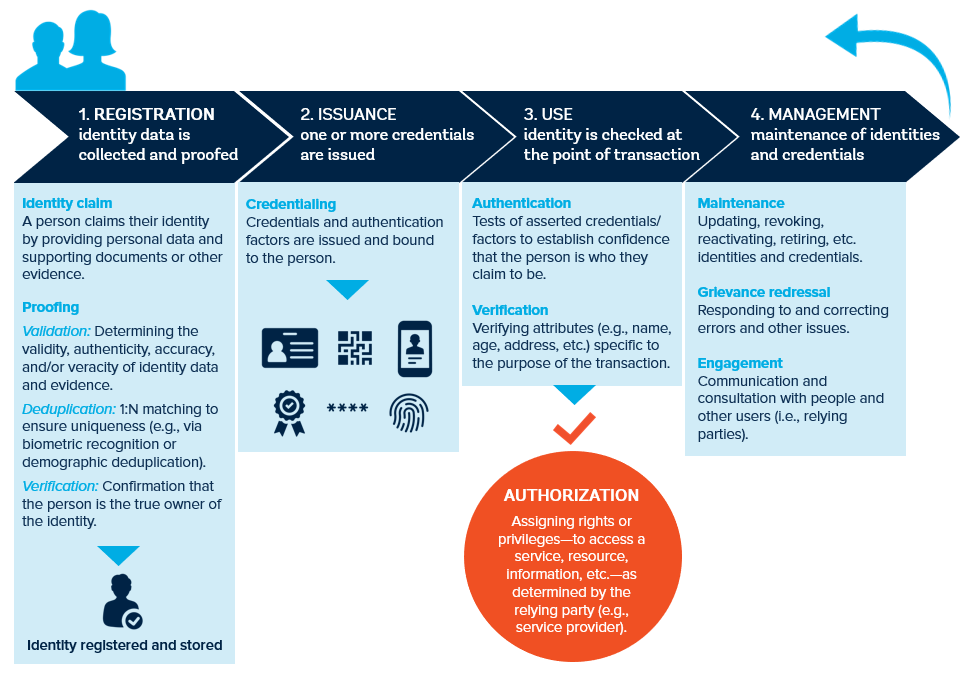
It has been well researched and documented that as the digital identity is managed securely and effectively throughout its lifecycle, from creation to deletion, and helps to protect against identity theft and fraud. Primary goal of all this is to ensure the user’s privacy is protected, that the user has control over their own digital identity and signing keys.
To ensure the proper management of digital identity throughout its lifecycle, eIDAS has established a framework of technical and operational standards, rules, and procedures for electronic identification, authentication, and trust services
The eIDAS generally recognizes that the identity lifecycle may be completed by a single actor, such as an ID authority, or split between multiple actors, including registration authorities and credential and authentication providers, in both public and private sectors.
Throughout the identity lifecycle, the State issuing the identity, QTSP/TSP/CA providing the trust services, or technology vendors like Methics who provide standards based solutions must comply with the eIDAS regulations and policy.
What eIDAS2 brings about Digital Identity lifecycle?
eIDAS 2 is an extension European Commission vision for a European Digital Identity Framework. The EUDIW (European Union’s Digital Identity Wallet) aims to provide EU citizens with a secure, user-friendly, and interoperable digital wallet that allows them to access public and private online services across the EU.
While the eIDAS 2 is still under legislative process, closing to the end, the European Commission prepared the architecture reference framework (ARF) for the implementation of the EUDI Wallets.
The lifecycle of an EUDIW involves several stages and interactions with Trusted List Providers.
The lifecycle of an EUDI Wallet will have some interactions with the Trusted List Providers that specify the status of a role in the EUDI Wallet ecosystem in a trustworthy manner. Wallet Providers which provide Digital Identity Wallet to European residents/citizens has three core objects: EUDI Wallet Solution, EUDI Wallet Instance, and PID (Personal Identification Data).
Image below lists the state chart for different components of EUDI Wallet Provider (EUDI Wallet Solution, EUDI Wallet Instance, and PID). EUDI Wallet Solution).
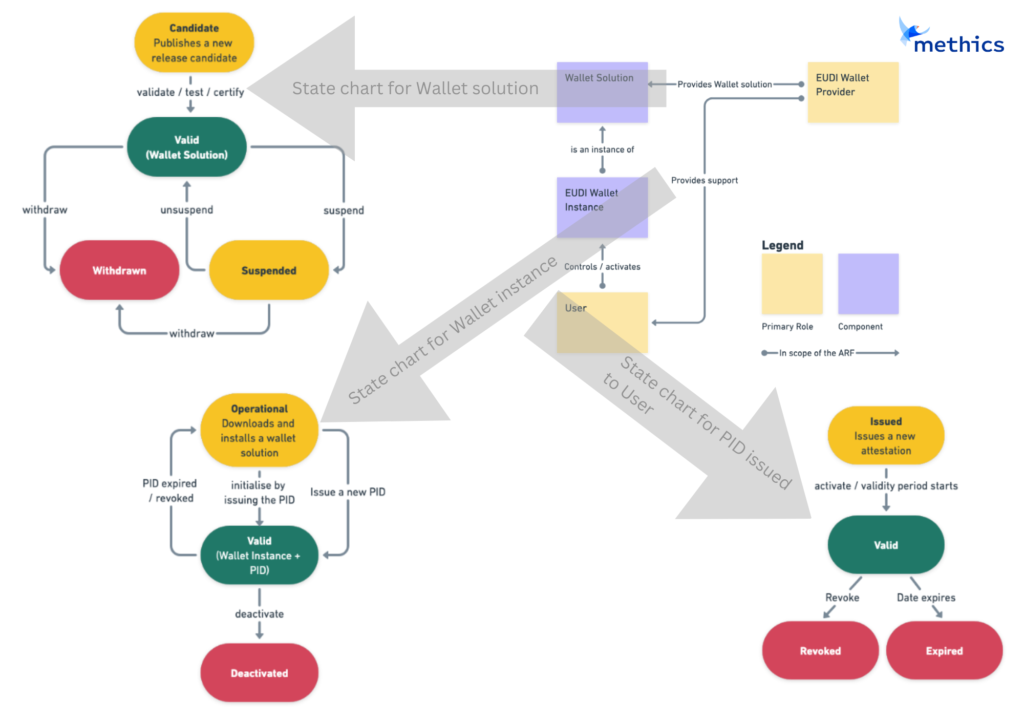
According to EU it is foreseen that by Q2 and Q3 2023 the Reference Implementation of different Wallet scope areas will be released.
The following three main elements define the EUDI Wallet life-cycle:
- EUDI Wallet Solution
- EUDI Wallet Instance
- Person Identification Data
1. EUDI Wallet Solution
- An EUDIW Solution is the complete product or service provided by an EUDI Wallet Provider
- EUDI Wallet Solution’s lifecycle begins in the “Candidate” state
- Upon meeting legal and technical criteria, a member state can decide to provide EUDIW Instances to users, and the solution enters the “valid” state
- A member state can temporarily suspend or unsuspend a solution under certain conditions, such as security issues. If necessary, the EUDI Wallet Solution can be completely withdrawn.
2. EUDI Wallet Instance
- The EUDI Wallet Instance is a personal instance (may consist of a single mobile app, or a set of local and remote components available to a specific user) of a EUDI Wallet Solution that belongs to and is controlled by the end-user (citizen)
- The EUDIW instance’s lifecycle starts with the user installing and activating a valid EUDIW solution
- The EUDI Wallet Instance can have two status:
- Operational (which not necessarily requires the PID and can be used for low LoA cases)
- Valid (used for EUDI specific functions, tied to a valid PID)
- Once initialized, it is considered valid as it is recognized by a PID provider and holds a valid PID set.
- If the PID expires or is revoked, the EUDIW instance’s state is downgraded to “operational,” which may affect the validity of a (Q)EAA or a certificate for Qualified Electronic Signature (QES).
- Users can deactivate their EUDIW instance, and this is separate from the possibility of a PID or (Q)EAA provider revoking their attestations.
3. Personal Identification Data
- Personal Identification Data (PID) is issued to a EUDIW Instance of the user
- The lifecycle of PID and Qualified Electronic Attestation of Attributes (QEAA) are similar
- A PID can be pre-provisioned, meaning it becomes valid at a later date. Once valid, a PID can either expire or be revoked by its provider, and it cannot return to a valid state after that.
Summary
In general, the eIDAS and eIDAS 2 directives underline the significance of overseeing the complete lifecycle of digital identities, guaranteeing the security, confidentiality, and correctness of identity data, and advancing compatibility across different identity systems and entities.
Methics is positioned to support the key stakeholders responsible for making the EUDIW a reality. As a global leader of open standard Mobile ID services, our products are delivering tech for strong authentication. Methics can integrate existing services and high level of assurance identity mechanisms to a new identity framework. We support digital identity over a wide variety of authentication mechanisms and security assertions. Methics will offer a bridge between traditional PKI and W3C decentralized identity projects to provide identity and signing services. Feel free to get in touch with us if you want to discuss the presented model and how SSCD/QSCD can be provided from EUDI wallet to European residents.
Publish Date: 26th April 2023
Written and Edited by: Ammar Bukhari & Jarmo Miettinen
References
- https://id4d.worldbank.org/guide/identity-lifecycle
- https://eu-digital-identity-wallet.github.io/architecture-and-reference-framework/arf.html
- https://www.enisa.europa.eu/publications/enisa-report-remote-id-proofing
- https://www.methics.fi/understanding-eidas-level-of-assurance/
Picture Credits: @VISUALITYEU
